Mobile IP Route Optimization
26.5.2000
Henrik Petander
Department of Electrical and Communications Engineering
Helsinki University of Technology
Henrik.Petander@hut.fi
Abstract
In standard IP routing routes are constantly optimized as
routing tables are propagated throughout the Internet. In the case of
mobile hosts that wish to use their home addresses this mechanism does
not work. Thus while communicating sub-optimal routing often takes
place. The problem results from the routing of packets to the mobile
node via its home agent. Route optimization enables the datagrams to
be routed directly in both directions. Route optimization also
provides support for smooth handoffs by letting the previous foreign
agent tunnel datagrams to mobile node's current location. Despite the
advantages provided by route optimization it is unlikely that it will
be deployed widely in the near future, due to its requirements for
correspondent nodes.
Contents
1 Introduction
2 Addition of Mobility Support to IPv4
2.1 Mobile IPv4 in general
2.2 Triangle routing
2.3 Bi-directional tunneling
3 Problems with Mobile IPv4
3.1 Sub optimal routes
3.2 Handoffs
3.3 Criteria for an efficient solution
4 Mobile IPv4 route optimization
4.1 Route optimization messages and data structures
4.2 The effect on static routes
4.3 Handoffs with route optimization
4.4 Security considerations
4.5 General deployment requirements
5 Mobile IPv6 and route optimization
5.1 Main characteristics of Mobile IPv6
5.2 The effect on routing
5.3 The effect on handoffs
5.4 Problems solved
6 Conclusion
Glossary
References
Further Information
1 Introduction
The introduction of portable computers and other mobile terminals with
wireless network adapters has created a new need for mobility management
in the Internet. In general users want to enjoy the same connectivity regardless
of their physical location. They do not want to reboot their computers
or restart their applications, even when they move from one network to
another. To achieve this in the TCP/IP world, the addition of a mobility
management protocol is needed. Some may argue that DHCP - Dynamic Host
Configuration Protocol [2] or some other dynamic addressing protocol is
a good enough solution. Even if these protocols do not require rebooting
of the terminal they still break higher-level protocol connections.
To achieve true mobility while using the TCP/IP protocol suite, the IP
protocol needs to be modified in a way that makes movement invisible to
the higher level protocols.
Mobility in wireless networks can be implemented also in the link-layer.
This makes it invisible to the network-layer and is often implemented with
proprietary protocols. A link-layer solution is easier to deploy, since
it requires changes only to the drivers of the network adapter whereas
network layer solutions require broader changes to the operating system
of the terminal. However, link-layer mobility is limited to a single subnetwork,
which limits its applicability to large-scale user mobility.
In Section 2 I present the basic Mobile IPv4 protocol [9] in general
and focus more deeply on its effect on routing. In Section 3 I discuss
the problems related to Mobile IPv4 and criteria for solutions to these
problems. In Section 4 I present route optimization and also analyze its
performance and feasibility as a solution. In Section 5 I present
Mobile IPv6 [4] and compare it to the route optimization in Mobile IPv4.
In section 6 I provide conclusions on route optimization based on
the analysis in Sections 4 and 5.
2 Addition of mobility support to IPv4
IPv4 was not designed with later addition of mobility support in mind.
The routing of datagrams is done with the network part of the IP-address.
Thus all the addresses must correspond to the network topology in order
for the nodes to be able to receive any datagrams from nodes in other subnetworks.
Addition of mobility support to IPv4 has been done on top of
the IP-layer to minimize the required changes to hosts and routers. The
signaling in mobile IPv4 is done with UDP datagrams.
2.1 Mobile IPv4 in general
Mobile IPv4 provides mobility support by allowing the mobile node to be
reachable via its home address regardless of its physical location. This
is achieved via tunneling of the datagrams to Mobile Node's current care-of
address. When the Mobile Node moves to a different subnetwork, it sends
a home registration to its home agent, which contains both the care-of
address and the home address of the mobile node. With this information
the home agent can capture and tunnel datagrams sent to the mobile node's
home address. The correspondent nodes do not need to be aware of
the mobile node's location, as the mobility is invisible to them.
The care-of address of the mobile node acts as the tunnel endpoint.
If the care-of address points to the mobile node it is called a co-located
care-of address. The mobile node acquires the co-located care-of address
via some mechanism, e.g., DHCP and sends a home registration request to
its home agent, which can then start tunneling datagrams to the new address.
In case the address points to a foreign agent it is called a foreign agent
care-of address. Foreign agents may act as tunnel endpoints and provide
mobility services for mobile nodes in foreign networks.
Upon entering the foreign network the mobile node first receives an
agent advertisement, which contains the foreign agent care-of address.
After this it sends a registration request to the foreign agent, which
sends it further to the mobile node's home agent. Finally the home
agent can tunnel packets to the foreign agent, which decapsulates them
and forwards the original datagram to the mobile node. [9]
2.2 Triangle routing
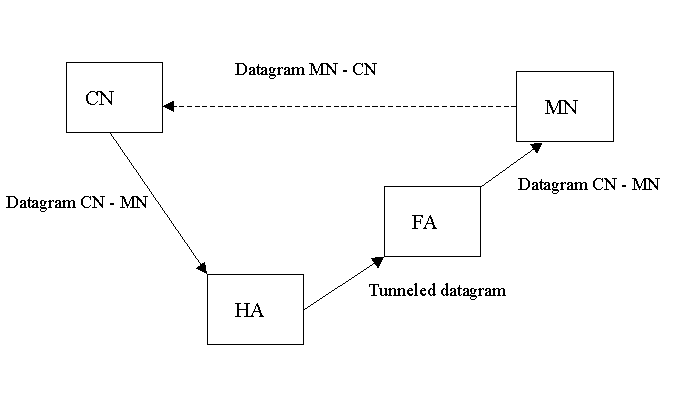
Triangle routing is the basic routing scheme with Mobile IPv4. In triangle
routing the mobile node sends its packets directly to the correspondent
node. The correspondent node sends all datagrams to mobile node's home
address. The home agent then tunnels them to mobile node's care-of address,
as illustrated in figure 1. To preserve transport-layer connections mobile
node uses its home address as the source address of all datagrams it sends.
Figure 1. Triangle routing with foreign agent care-of address.
2.3 Bi-directional tunneling
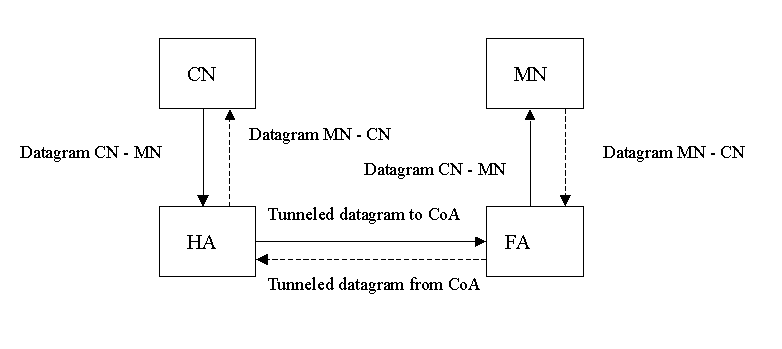
As the mobile node moves away from its home network it still continues
to receive its packets via the home agent. In the case of bi-directional
tunneling it also sends its packets via the home agent. The mobile node,
or the foreign agent as in Figure 2., encapsulates the original datagram
by adding a new header to it with the home agent's address as the destination
address and the care-of address as the source address. Thus all traffic
to and from the mobile node is routed via the home agent. This makes the
mobility invisible to the correspondent nodes. However bi-directional tunneling
with IP-IP tunneling adds 20 bytes of overhead to each packet sent by the
mobile node, when compared to triangle routing. [8]
Figure 2. Bi-directional tunneling with foreign agent care-of address.
3 Problems with Mobile IPv4
3.1 Sub optimal routes
Both bi-directional tunneling and triangle routing lead to sub-optimal
routes. Although triangle routing provides optimal routing from mobile
node to correspondent node, it also leads to asymmetrical delays. The use
of the home address as the source address in foreign networks is a questionable
mechanism in the Internet of today, since routers performing ingress filtering
will drop datagrams with a topologically incorrect source address [3].
In case the mobile node is on another continent than its home agent, the
route from correspondent node to the mobile nodes via the home agent can
cause long delays and also unnecessary network congestion.
Both schemes also consume extra bandwidth, due to the tunneling from
the home agent to the care-of address that is used in both schemes. This
can be partly alleviated with other tunneling techniques, which use smaller
tunneling headers than IP-IP tunneling, such as minimal encapsulation [10].
Also header compression can be used to compress the inner header [1]. However,
if a co-located care-of address is used, the tunneling is done also over
the limited bandwidth radio medium between the network access point and
the mobile node. With typical 572 byte IP datagrams this leads to a large
overhead and wasted bandwidth.
3.2 Handoffs
Mobile IP was not designed for fast moving hosts. This is apparent in the
movement detection algorithm in the specification, which contains two methods,
which both are rather slow. The home agent handles all handoffs, although
it may be far from the current network of the mobile node. The network
delay adds to slow handoffs. Slow handoffs cause often packet loss, which
is especially harmful to real-time applications, such as voice over
IP or video streaming. TCP-based connections also suffer, since lost packets
may be mistaken for congestion and result in TCP's slow start mechanism
[9].
Since the home agent handles handoffs, they cause lots of signaling
traffic between the mobile node and the home agent. In high speed LANs
this is not an issue, but when low speed WANs are involved and lots of
mobile nodes are performing simultaneous handoffs, network congestion may
result.
3.3 Criteria for an efficient solution
An efficient routing scheme would use direct routes between the mobile
node and the correspondent node. It would also introduce minimal overhead
for delivering the data and signaling information. Handoffs would
be performed with minimal packet loss. With localized handling of the handoffs
can be performed somewhat faster, since the network delay between mobile
node and home agent does not effect the handoff. Thus localization of handoffs
would be a part of a good solution.
In addition to being technologically optimal, the solution, or protocol,
should also be feasible. It should not require large changes to the operating
systems of the correspondent nodes and it should also be interoperable
with the specifications of the TCP/IP protocol suite.
4 Mobile IPv4 route optimization
Mobile IPv4 route optimization [11] is a proposed extension to the Mobile
IPv4 protocol. It provides enhancements to the routing of datagrams between
the mobile node and to the correspondent node. The enhancements provide
means for a correspondent node to tunnel datagrams directly to the mobile
node or to its foreign agent care-of address.
4.1 Route optimization messages and data structures
The route optimization extension adds a conceptual data structure, the
binding cache, to the correspondent node and to the foreign agent. The
binding cache contains bindings for mobile nodes' home addresses and their
current care-of addresses. With the binding the correspondent node can
tunnel datagrams directly to the mobile node's care-of address.
Every time the home agent receives a datagram that is destined to a
mobile node currently away from home, it sends a binding update to the
correspondent node to update the information in the correspondent node's
binding cache. After this the correspondent node can directly tunnel packets
to the mobile node. Thus direct bi-directional communication is achieved
with route optimization, as shown in Figure 3.
Figure 3. Direct routing with route optimization and foreign agent
care-of address.

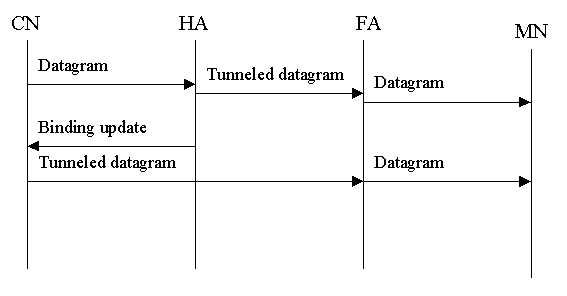
Route optimization adds four new UDP-messages to the Mobile IPv4 protocol:
-
Binding update informs the correspondent node or foreign agent of the mobile
node's new location. It is sent by the home agent or in the case of previous
foreign agent notification, by the new foreign agent, as shown in Figure
4. The binding update contains the care-of address and the home address
of the mobile node and also the lifetime of the binding. It also must contain
a mobile IP authentication extension. An identification number may also
be present to provide a way of matching updates with acknowledgements and
to protect against replay attacks.
-
Binding acknowledgement is sent by the correspondent node or the foreign
agent in response to the binding update. It contains the mobile node's
home address and a status code. It also contains an identification number,
if there was one in the corresponding binding update.
-
Binding request is sent by the correspondent node to the home agent to
request a binding update. It contains the home address of the queried mobile
node and possibly an identification number.
-
Binding warning is sent by the previous foreign agent in response to receiving
a tunneled datagram for a mobile node for which it has a binding and for
which it is not acting as the current foreign agent. The binding warning
is sent to the home agent. It contains the home address of the mobile node
and the address of the correspondent node that does not have up to date
information of the mobile node's current care-of address. With this information
the home agent can send a binding update to the correspondent node.
-
Figure 4. Binding update to correspondent node
-
4.2 The effect on static routes
As the correspondent node learns the care-of address of the mobile node
from the binding update, it can tunnel datagrams directly to the mobile
node's care-of address [11]. Thus only the first datagrams are routed via the
home agent. This reduces the network load and also reduces the delays caused
by routing. Thus the optimization is valuable to mobile nodes that visit networks located far from their home agent.
However, the overhead caused by tunneling is not decreased. The
correspondent node's use of minimal encapsulation [10] is a partial remedy,
if both the encapsulator and the decapsulator support it. Ingress
filtering [3] may also prevent the mobile node from sending datagrams
directly to the correspondent node. The use of direct reverse
tunneling from the care-of address to the correspondent node's address
is a possible solution to ingress filtering. However, it is not
possible with foreign agent care-of addresses, since the current
reverse tunneling standard [8] requires the foreign agent to tunnel
all packets to the home agent of the mobile node.
4.3 Smooth handoffs with route optimization
In the static case the protocol is fairly simple, but handoffs somewhat
complicate the situation. When the correspondent node has an out of date
entry for the mobile node's care-of address it tries to send the tunneled
datagram to the mobile node's previous location and the datagram is lost.
To solve this problem the protocol includes the previous foreign agent
notification mechanism, which adds a binding cache to the foreign agent. [3]
When a mobile node moves to a new subnetwork it sends a
registration
request to the new foreign agent. The registration
request may contain
a previous foreign agent notification
extension. Upon receiving such a
request the foreign agent builds a
binding update and sends it to the previous foreign agent. The
previous foreign agent can then, after authenticating the update,
create a binding for the mobile node. With this binding it can
re-tunnel datagrams to the mobile node's new care-of address. The
re-tunneling requires foreign agent care-of addresses in order for the
agents to act as tunnel endpoints. [3]
The previous foreign agent notification mechanism provides temporary
localization of the handoffs. It does not reduce the signaling load
between the home agent and the mobile node, but reduces the number of
datagrams lost due to correspondent nodes with out-of date bindings.
4.4 Security considerations
Since the correspondent nodes and foreign agents have binding caches, which
change the routing of datagrams destined to mobile nodes, the binding updates
must be authenticated. The authentication is performed in a similar manner
as in base Mobile IPv4. All binding updates contain a route optimization
or smooth handoff authentication extension. This extension contains a hash,
which is calculated from the datagram and the shared secret. [11]
The correspondent node and the mobile node's home agent need a security
association [5]. This association is used for the authentication of the
binding updates. Since the mobile node sends a binding update directly
to its previous foreign agent, they also need a security association. If
the security associations are not preconfigured they can be established
via a key management protocol such as ISAKMP [6] or SKIP [7]. [11]
4.5 General deployment requirements
In order to make use of the binding updates the correspondent nodes must
be able to process and authenticate them and be able to encapsulate datagrams [11].
To establish this the network stacks of the operating systems require
changes. Since correspondent nodes need to establish a security association
with the home agent and foreign agents need to establish one with the mobile
node, a widely deployed key management system is obviously needed.
Otherwise only nodes with statically configured security associations can
benefit from the binding updates.
5 Mobile IPv6 and route optimization
5.1 Main characteristics of Mobile IPv6
Whereas Mobile IP was added on top of the IPv4 protocol, in IPv6 mobility
support is built into the IP-layer [4]. In mobile IPv6 route optimization
is an essential part of the protocol. Mobile nodes have a binding update
list, which contains the bindings other nodes have for it. Correspondent
nodes and home agents have a binding cache, which contains the home and
care-of addresses of mobile nodes they have been recently communicating
with. All signaling is performed via destination options that are appended
to the base IPv6 header. Thus all signaling traffic can be piggybacked
on datagrams with a data payload, as in Figure 5.
Figure 5. Destination option.
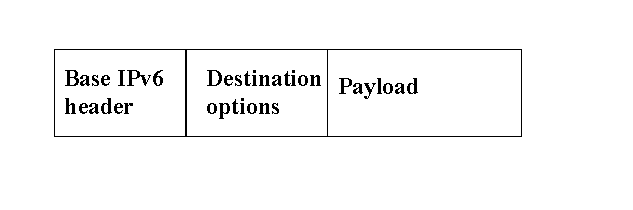
The destination options are:
-
Binding update option, which is sent by the mobile node to its home agent
and correspondent nodes to inform them of a change of location.
-
Binding acknowledgement option, which is sent in response to the binding
update.
-
Binding request option, with which a node can request a new binding update
from the mobile node, when the binding is about to expire.
-
Home address option, which the mobile node appends to all datagrams it
sends while away from its home network. The home address option is used
to avoid the negative effects of ingress filtering by using the topologically
correct care-of address as the source address and including the home address
in the option. The receiving node will then copy the home address to the
source address before passing the packet to any transport level protocol.
All care-of addresses in Mobile IPv6 are co-located; thus foreign
agents are not a part of the protocol. Since all nodes are only required
to understand the home address option, triangle routing will occur also
with mobile IPv6. However, if the correspondent node implements the draft
fully, only the first datagrams it sends will be routed via the home agent.
The mobile node always sends a binding update to the original sender of
a tunneled datagram. With this binding the correspondent node can
send datagrams directly to the mobile node using a routing header. A datagram
with a routing header contains the care-of address as the destination address
and the home address in the routing extension header as the final destination.
Thus the datagram will be normally routed to the care-of address. When
the mobile node receives a datagram with a routing header it swaps the
final destination with the destination address field. The home address
option and the routing header make the mobility transparent with direct
routing. [4]
5.2 The Effect on Routing
By using direct routes in both directions the consumption of network resources
is minimized. The 40-byte IPv6 headers consume extra bandwidth when
compared to 20 byte IPv4 headers. However the use of routing header and
home address option removes the need for constant tunneling, thus decreasing
the bandwidth consumption. Although they both add overhead to packets they
still are considerably smaller than IPv6 headers, which would be
used in tunneling. The destination options used for signaling can be piggybacked [4]
which decreases the signaling overhead considerably, since the options
are relatively small when compared to UDP packets.
5.3 The effect on handoffs
The IPv6 mobility support provides the previous router notification mechanism,
with which the amount of lost of packets in handoffs can be reduced [4]. In
IPv6 the mobile node sends a binding update directly to the previous router,
which consumes more bandwidth but is faster than the mechanism used with
Mobile IPv4 route optimization.
5.4 Problems solved
Mobile IPv6 provides improvements on routing and signaling efficiency.
As the signaling can be mostly piggybacked on data packets there will be
considerably less signaling overhead between the mobile node and the correspondent
nodes than in mobile IPv4 route optimization between the home agent and
the correspondent nodes. The minimum requirements for the correspondent
node provide at least triangle routing even in the worst case, since care-of
address can be used as the source address. Hosts that are likely to communicate
with mobile nodes will probably implement the binding cache and communicate
directly with the mobile node. In both cases the routing saves network
capacity and decreases delays, when compared to reverse bi-directional
tunneling between the mobile node and correspondent node.
The key management problem is not solved Mobile IPv6 does not solve
the key management problem, but the integration of IPSec [5] into IPv6
is likely to result in support for key management protocols in most operating
systems implementing IPv6.
6 Conclusion
With the increasing number of mobile hosts optimal routes are a goal worth
striving for. Route optimization provides means for direct routes between
the mobile node and its correspondent nodes. Technology-wise it provides
a good framework of techniques to support direct routes. Deployment-wise
it is rather problematic. It requires rather large changes to the operating
systems of the correspondent nodes. It also requires a trust relationship
between the correspondent node and the home agent of the mobile node. As
a result of these requirements it probably will not be widely deployed
in the near future. The situation will most likely change with the possible
transition to IPv6, since mobility support will be a part of the protocol
specification at that time. Thus route optimization will probably gain
widespread support only via Mobile IPv6.
Glossary
|
CN
|
Correspondent node, any node communicating with the mobile node
|
|
FA
|
Foreign agent provides mobility services to mobile nodes in a
foreign network
|
| HA |
Home agent provides mobility services in the mobile node's home
network
|
|
IP
|
Internet protocol is the network layer protocol used in the TCP/IP
protocol suite.
|
| IPSec
|
IP layer security protocol |
|
ISAKMP
|
Internet security association and key management protocol
is used to establish security associations
|
|
LAN
|
Local area network is a high speed physical network connecting
nodes
|
| MN
|
Mobile node is a node capable of changing its location invisibly
to any transport level connections
|
| SKIP |
Simple Key Management for Internet Protocols |
| TCP |
Transport control protocol is a connection oriented transport
protocol |
| UDP |
Universal datagram protocol, a connectionless transport protocol |
| WAN |
Wide area network is a relatively low speed physical network |
References
| [1] |
Degermark M., Nordgren B.,
Pink S., IP Header Compression RFC 2507, February 1999
<http://www.ietf.org/rfc/rfc2507.txt> |
| [2] |
Droms R., Dynamic Host Configuration Protocol, RFC 2131, March 1997
< http://www.ietf.org/rfc/rfc2131.txt
> |
| [3] |
Ferguson P., Senie D., Network Ingress Filtering: Defeating Denial
of Service Attacks which employ IP Source Address Spoofing, RFC 2267, January
1998
<http://www.ietf.org/rfc/rfc2267.txt> |
| [4] |
Johnson D., Perkins C., Mobility
Support in IPv6, work in progress, 22 October 1999
<http://www.ietf.org/internet-drafts/draft-ietf-mobileip-ipv6-09.txt> |
| [5] |
Kent S., Atkinson R., Security Architecture for the Internet Protocol,
RFC 2401, November 1999
<http://www.ietf.org/rfc/rfc2401.txt> |
| [6] |
Maughan D., Schertler M., Schneider M., Turner J., Internet Security
Association and Key
Management Protocol (ISAKMP), RFC 2408, November 1998
<http://www.ietf.org/rfc/rfc2408.txt> |
| [7] |
Montenegro G., Gupta V., Sun's SKIP Firewall Traversal for Mobile IP,
RFC 2356, June 1998
<http://www.ietf.org/rfc/rfc2356.txt> |
| [8] |
Montenegro G., Reverse Tunneling for Mobile
IP, RFC 2344, May 1998
<http://www.ietf.org/rfc/rfc2344.txt> |
| [9] |
Perkins C., IP Mobility Support for
IPv4, RFC 2002, October 1996
<http://www.ietf.org/internet-drafts/draft-ietf-mobileip-rfc2002-bis-00.txt
> |
| [10] |
Perkins C., Minimal Encapsulation within
IP, RFC 2004, October 1996
<http://www.ietf.org/rfc/rfc2004.txt> |
| [11] |
Perkins C., Johnson D.,
Route Optimization in Mobile IP, work in progress
< http://www.ietf.org/internet-drafts/draft-ietf-mobileip-optim-09.txt
> |
| [12] |
Van Jacobson, Congestion Avoidance and Control. In Proceedings
of the SIGCOMM '88 Symposium: Communications Architectures &
Protocols, pages 314--329, August 1988. |
Further Information
-
A good introductory paper on mobility issues and Mobile IP by Charles Perkins:
< http://www.baltzer.nl/monet/articlesfree/1998/3-4/mnt071.pdf
-
Comer's book, Internetworking with TCP/IP, published by Prentice Hall,
provides a good introduction to the TCP/IP protocol suite.
-
The current IETF-drafts and RFCs can be found from IETF's web site:
< http://www.ietf.org/html.charters/mobileip-charter.html
>
-
More in-depth information can be found from the mobile IP mail archive
at Nortel networks web site:
< http://www17.nortelnetworks.com/archives/mobile-ip.html
>




