
T-110.5200 Laboratory Works on Information Security (4 cr)
Lab 5: VPN
IP Security Architecture
This assignment introduces you to the Virtual Private Network (VPN) concept. You will use IPsec to establish a VPN in practice by creating and examing a host-to-net VPN scenario (see the figure below). A roadwarrior host (RW) establishes a secure tunnel to a gateway (GW). Traffic can flow from the roadwarrior through the gateway to a client (C) and back. Other hosts on the right-side local link can not see the traffic flowing inside the tunnel. The goal of this assignment is you to test communication between the client and the roadwarrior by succesfully pinging and tracerouting each host in both directions. The IPSec tunnel mode is used in this assigment. In addition, RSA private keys are used as secrets.
The notation xxx(y) in this document means the relevant UNIX manual pages in that phase. Use the command man y xxx to read them.
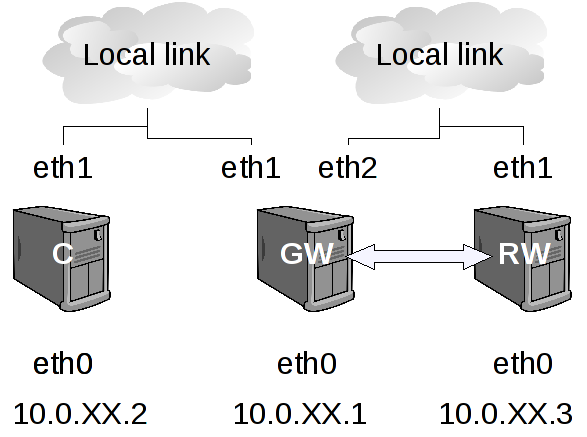
Client, Gateway, and Roadwarrior
Set up the interfaces of the client, the gateway, and the roadwarrior hosts. Verify that you can ping the gateway from the other hosts, and that you can not ping the roadwarrior from the client or vice versa. Write down the network configuration.
ifconfig (8), ping (8)
Examine the OpenSWAN configuration on these hosts. The hosts have OpenSWAN installed, but not yet fully configured. Examine the example ipsec configuration files /etc/ipsec.conf and /etc/ipsec.secrets.
ipsec.conf(5), ipsec.secrets(5)
In a case that you can not find existing secrets, you can use the following command on the gateway and on the roadwarrior hosts:
ipsec newhostkey --verbose --bits 256 --output /etc/ipsec.d/gw-rw.secrets.
Print the corresponding public key on each host: ipsec showhostkey --left.
ipsec(8)
Command ipsec barf also gives lots of information about the IPSec subsystems and configuration files.
Update:
You can uncomment the line:
# plutodebug="control parsing"
in ipsec.conf to get more debug information.
Question set 1:
| 1.1 | What is the purpose of the two files? How they need to be protected? | 2 p |
| 1.2. | What do the terms "left" and "right" stand for in the configuration files? | 1 p |
| 1.3 | Explain the following parameters that can be set in the ipsec.d/*.conf or ipsec.conf : leftid, leftrsasigkey, leftsubnet, rightsourceip . | 4 p |
| 1.4 | What is wrong with the given command to create the secret? | 1 p |
Copy templates of ipsec.d/gw.conf and ipsec.d/rw.conf from here and place them in the right places on the virtual machines.
| conn road left= leftid= leftrsasigkey= leftsubnet= right=%any rightid= rightsourceip= rightrsasigkey= auto=add |
| conn road left= leftid= leftsourceip= leftrsasigkey= right= rightsubnet= rightid= rightrsasigkey= auto=add |
On the gateway, use commands sysctl -w net.ipv4.ip_forward=1 and sysctl -w net.ipv4.conf.all.rp_filter=0
sysctl(8)
Edit the gw.conf and rw.conf files according to your network configuration.
ipsec.conf(5)
Restart the IPSec subsystems using the command /etc/init.d/ipsec restart on the gateway and on the roadwarrior.
Question set 2:
| 2.1 | Describe your network configuration. What IPs you assigned to the interfaces (in total 4 interfaces) of each of the three host? | 2 p |
| 2.2. | What network address space you assigned to the subnetwork behind the gateway where the client resides? How does this correspond to the leftsourceip parameter in the roadwarrion configuration? | 2 p |
Establish security associations (SA)
You must initiate the IPSec SA handshakes from the roadwarrior. Use command ipsec auto --up road .
ipsec_auto(8)
To stop the connection, use the command ipsec auto --down road .
You can use command ipsec auto --status to check the current connection status and command setkey -D to view the security associations.
Update. You may also print the current IPSec policies by using command ip xfrm policy list.
setkey(8), ip (8)
If the security associations were correctly created, you can try to ping and traceroute the hosts (in both directions). Use tcpdump to view the network traffic on each host.
Question set 3:
| 3.1 | What details can you find about the security associations? How security associations are identified? Include the output from the previous commands. | 3 p |
| 3.2. | Give an example of the output of tcpdump when examining traffic over the IPSec tunnel. | 1 p |
| 3.3 | What is wrong with the current configuration? | 2 p |
On the gateway, use commands sysctl -w net.ipv4.conf.eth1.proxy_arp=1 and route add "sourceip of the roadwarrior"/32 lo. Again use ping and traceroute (in both directions). Use tcpdump to view the network traffic on each host.
arp(7), route(8)
Question set 4:
| 4.1 |
How did the previous commands change your configuration? Use arp -an on the client host to view the ARP entries. How does one of the entries correspond to the gateway? | 3p |
| 4.2 |
Give an example of the output of tcpdump when examining traffic over the IPSec tunnel. | 1 p |
| 4.3 | Why the output is slightly different when pinging and tracerouting the client and roadwarrior hosts from different directions? | 2 p |
arp(8)
Question set 5:
| 5 |
Once you are satisfied with the VPN configuration, run ipsec barf and attach the output to your answer file. | |
| 5.2 |
How would you improve this assignment? Did you have any problems in following the instructions? | extra 2 p |

